May 03, 2023
Discover the Secrets of I2P Darknet with Cocorico Link

Have you ever wondered what sets i2pd and Kovri apart? While some may suggest waiting for a clear answer, let's take a closer look at these two options within the realm of I2P darknet.
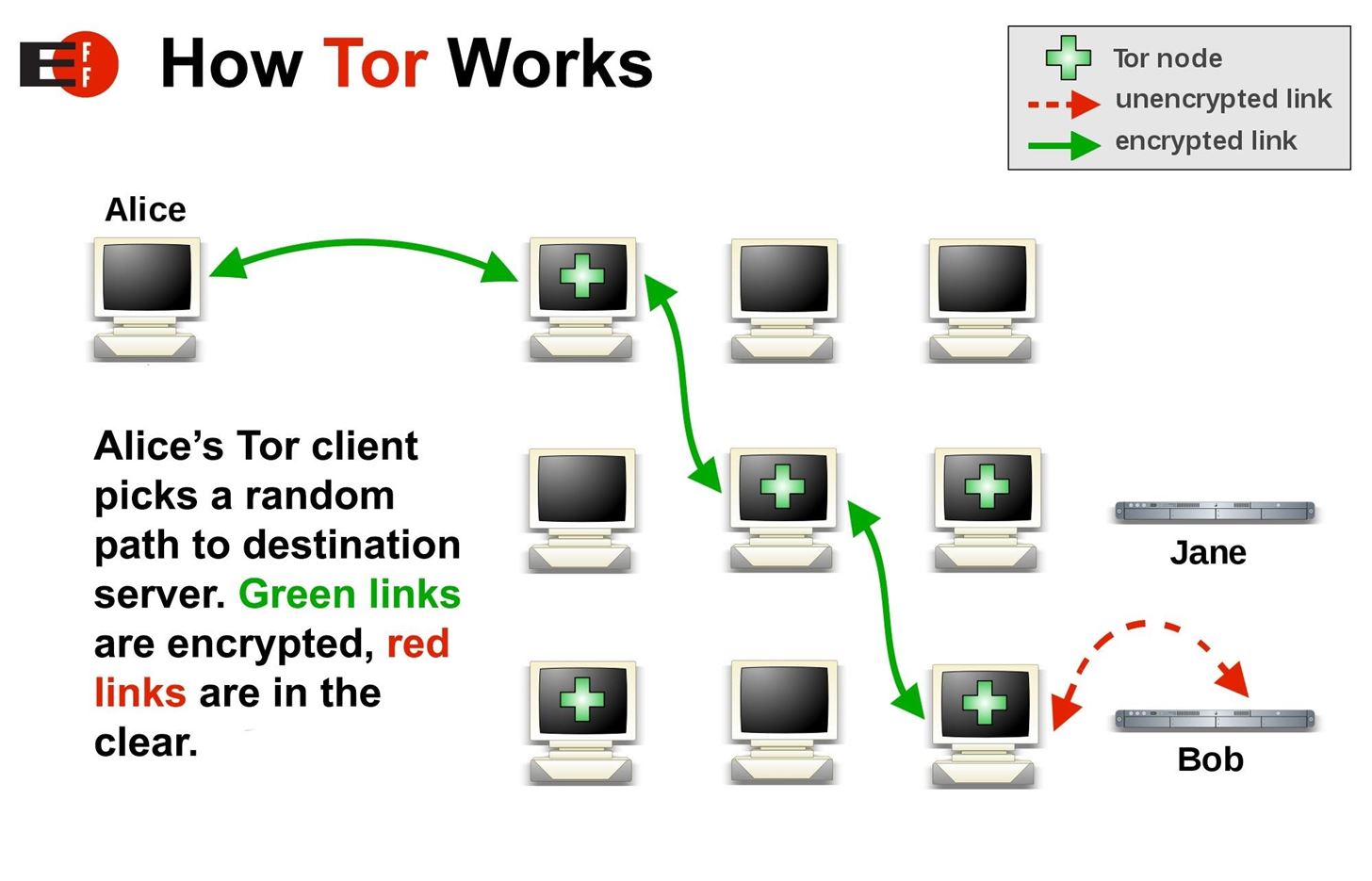
I2p darknet, also known as "Invisible Internet Protocol Daemon", is a great option for accessing the visible web anonymously without the fear of ISPs logging user chats. It is a free service similar to Tor, but its limited number of outproxies means that it may not be as anonymous when used for accessing the visible web. Nevertheless, I2p darknet is a reliable option for users who value their online privacy and want to stay anonymous on the internet.
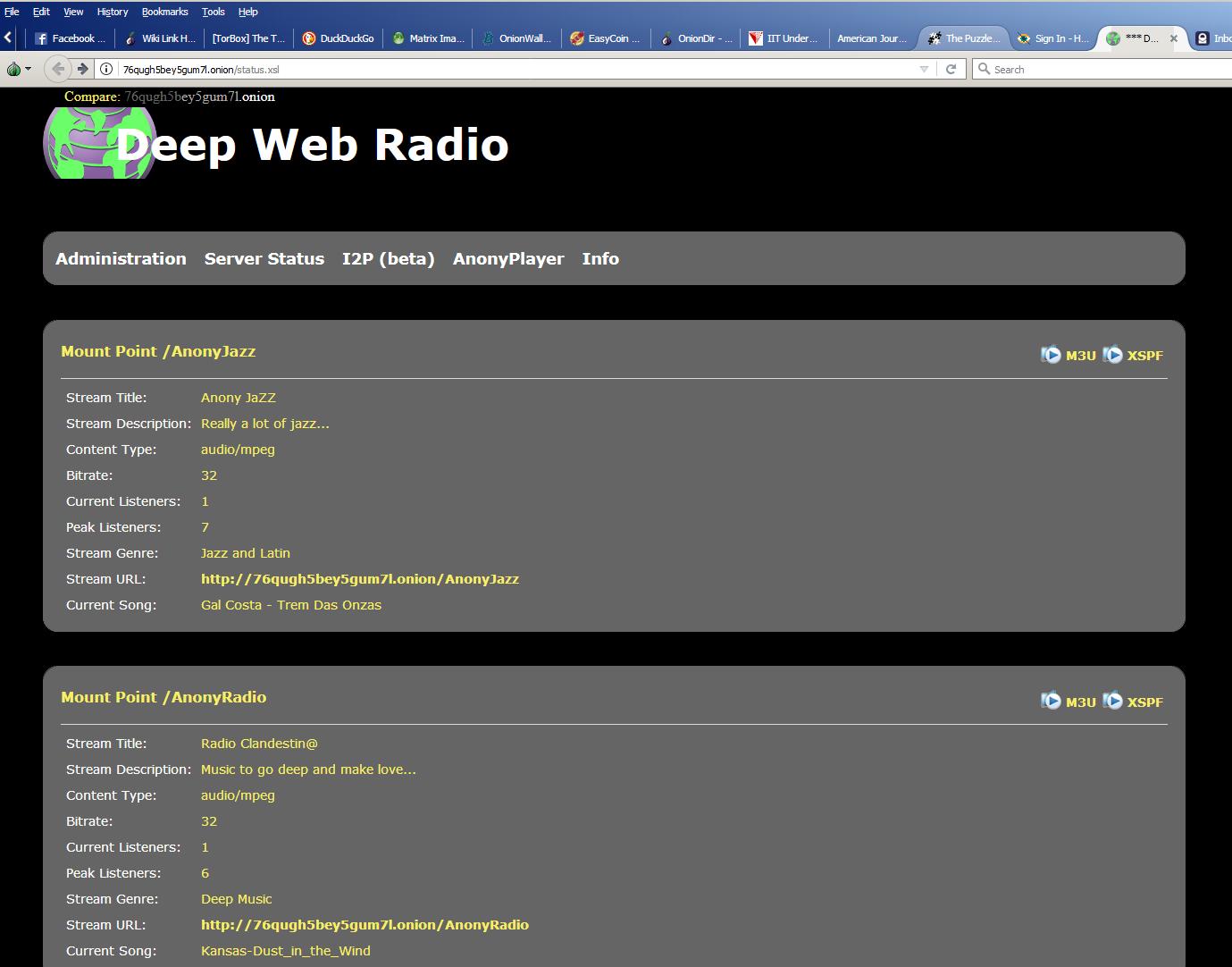
Discover the Cocorico Market URL on the I2P Darknet
"0.9.22 Release" has been archived from its original source and can be found on GitHub, as of November 2, 2017. This release pertains to I2P darknet.
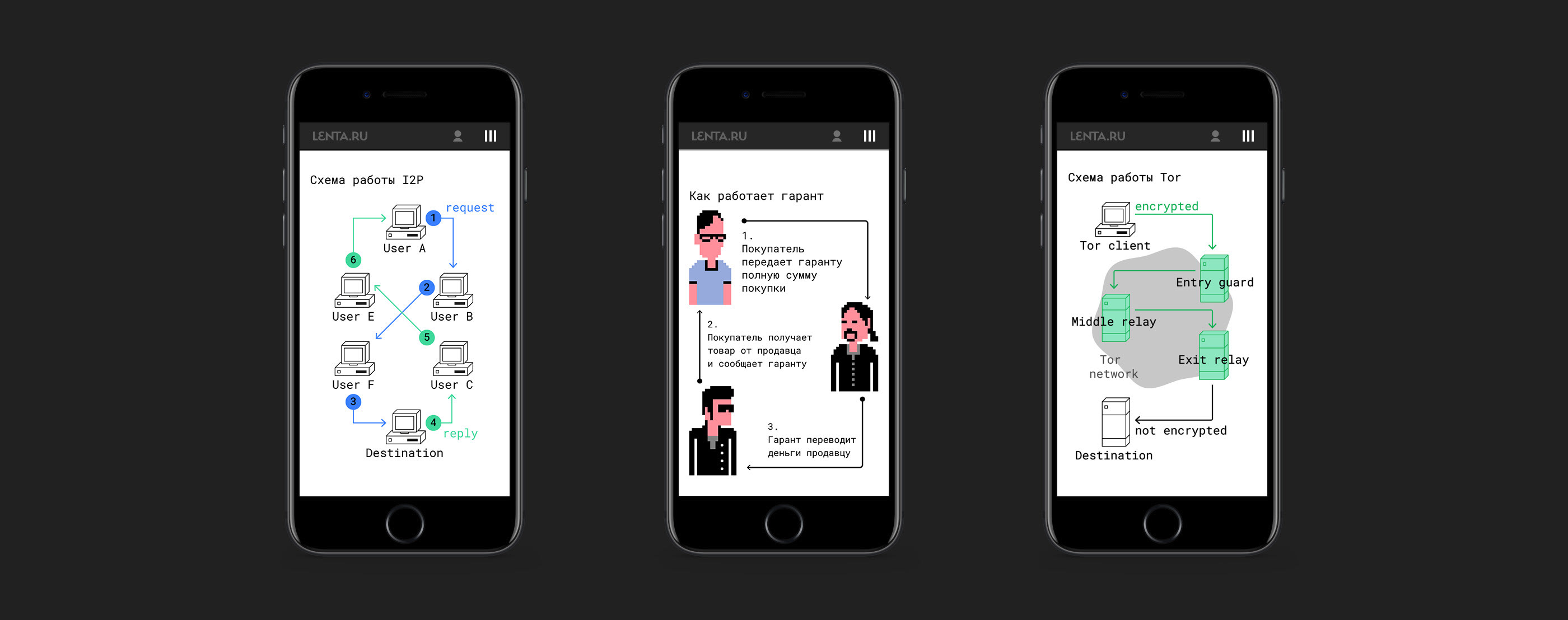
"I2P Darknet" is a term used to describe a network of computers that use the Invisible Internet Project (I2P) software to communicate anonymously and securely. This network is often used by individuals who want to avoid surveillance and censorship, as well as those who are interested in accessing content that is not available on the regular internet. The I2P software works by encrypting all traffic and routing it through a series of nodes, making it difficult for anyone to trace the origin or destination of the communication. While the I2P Darknet has been associated with illegal activities, such as drug sales and hacking, it is also used by activists and journalists to communicate securely and avoid government surveillance. Overall, the I2P Darknet provides a valuable service for those who want to protect their privacy and access information freely.
Discovering the Hidden World of I2P Darknet through Cocorico Url
On September 15, 2015, an article was published discussing the I2p darknet. Unlike Tor, which was created for anonymous access to the visible internet, I2p was specifically designed for anonymous access to the darknet. This technology was discussed in Computerworld.
The I2P darknet enables access to a variety of online services including Usenet, email, IRC, file sharing, Web hosting and http, as well as more traditional distributed applications such as BitTorrent. It is a network that allows users to communicate and share information anonymously, encrypting data and routing it through multiple nodes to prevent tracking of the source and destination of the communication. While its association with illegal activities such as drug trafficking and child pornography is well-known, the I2P darknet also serves a legitimate purpose of protecting the privacy of activists and journalists in countries with oppressive governments. Overall, it provides a level of anonymity and privacy that is unmatched by the regular internet.
As an experienced copywriter, I can rewrite the text on "I2p darknet" in English. Here's my version:
In this write-up, we'll delve into the intricacies of I2P and its various substitutes, examining their respective advantages, drawbacks, and disparities in great detail. Tune in to the Opt Out Podcast to learn more about this fascinating topic. Don't forget to keep an eye out for updates from the I2P Dev Team.
I2P darknet boasts a higher level of security compared to Tor, thanks to its unique architecture.
The I2P darknet has recently released version 0.9.11 of its software. This release includes various updates and improvements to enhance the user experience and security. The I2P darknet provides a secure and anonymous network for users to communicate and share information without being tracked or monitored by government agencies or third parties. With the new release, users can expect faster speeds and improved reliability. The I2P darknet continues to be a popular choice for those who value online privacy and security.
I2P Darknet
I2P Darknet is another option for those seeking anonymity and privacy online. It is a network within the internet that allows users to communicate and share information without revealing their identities. Unlike VPN and Tor, I2P Darknet provides a decentralized and encrypted environment, making it even more secure. It also offers additional features such as anonymous email and file sharing. If privacy is your top priority, I2P Darknet may be the solution for you.
Discover the Secrets of I2p Darknet - The Hidden Depths of the Deep Web
The I2P dark web tor darknet website is heavily geared towards a technical audience, lacking clarity for beginners. Every ten minutes, a link is established between the user's device and another peer.
Retrieved zzz (12 December 2016).
I2P is a darknet network that offers anonymity to its users through a layered encryption system. The network is decentralized and relies on volunteers to run nodes, making it incredibly difficult for any one entity to control or shut down the entire network. I2P is often used for secure communication, file sharing, and website hosting. The network can only be accessed through a specialized browser known as the I2P router, which allows users to access hidden services and communicate with other I2P users anonymously. While I2P has been associated with illegal activities in the past, it is also used by journalists, activists, and others who require a high level of privacy and security in their online activities.
The I2p darknet is becoming increasingly popular as the most secure way for communication. Although the old version (0.9.26) is no longer maintained, there has been a major upgrade to the native crypto library and a new addressbook subscription protocol with signatures. Additionally, there have been significant improvements to the Debian/Ubuntu packaging. This information was archived from the original source on September 9th, 2020.
The I2p darknet database is partitioned into several routers known as "floodfill routers". To access them, navigate to Firefox - Options - Advanced tab - Network tab - Connection Settings. Version.9 is now obsolete and not supported. On the other hand, version 22 addresses the issue of I2PSnark getting stuck before completion and initiates the transfer of router information to newer and more robust Ed25519 signatures.
Explore further
Distributed by Nemesis1386, LLC.