May 03, 2023
Unveiling the Secrets of the Dark Web: An Insight into Tor

Monitoring the dark web has become a crucial aspect of cyber intelligence. With Acid Cyber Intelligence, you don't need to sign up for an account - simply enter your email address on the homepage and you're good to go. This service scours social networks, criminal sites, chat systems, the deep web, and the dark web to gather threat intelligence. Specifically, their dark web scanning tool uncovers information on disclosed credentials. Keep your organization safe by staying one step ahead of potential threats with Acid Cyber Intelligence.
In the current age of frequent data breaches and cyber attacks, monitoring the dark web has become a crucial aspect for both individuals and organizations. If you want to know how to secure your passwords, we recommend checking out our guide. ATO protection focuses on safeguarding business accounts that are used to access their resources, including network logins and user accounts for websites.
If you want to monitor the dark web, having an Intrusion Detection System (IDS) installed on your network is essential. An IDS will help you detect any suspicious activity and alert you in real-time. It can also provide you with valuable insights into the types of threats that are targeting your organization on the dark web. With an IDS in place, you can stay one step ahead of cybercriminals and protect your sensitive data from being compromised.
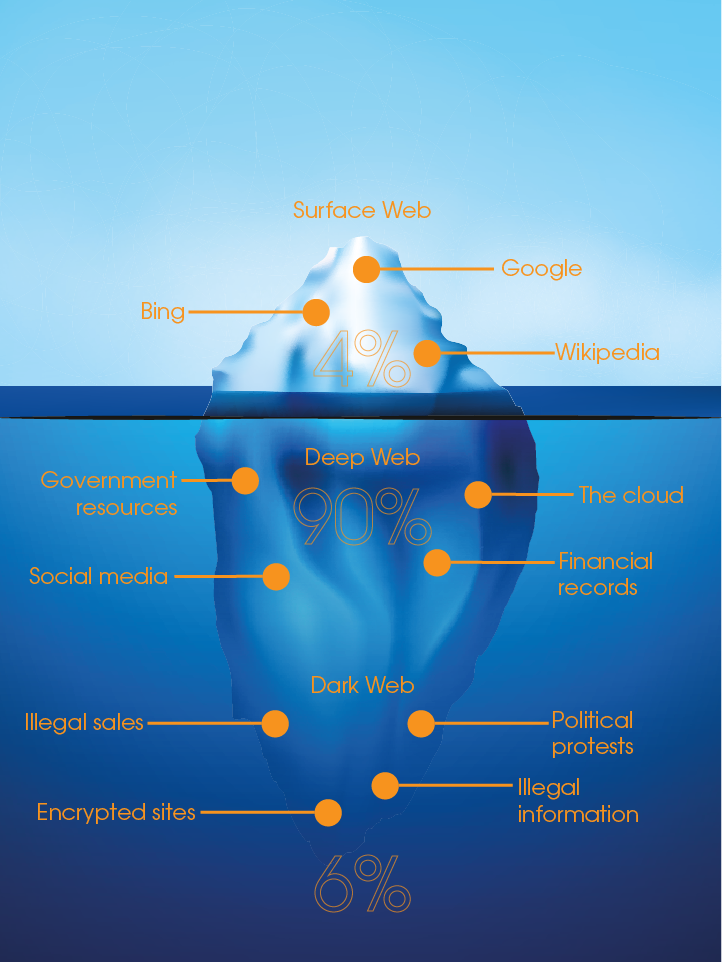
Monitoring the dark web is becoming increasingly important in today's digital age. Tor, an offshoot browser, is commonly used to access the dark web. To ensure security, a password manager can be used to generate highly secure passwords that are stored in an encrypted database. Additionally, web page requests are encrypted multiple times and can only be decoded by a computer holding the necessary key. This multi-layered encryption adds an extra layer of protection for those monitoring the dark web.
Decoding the Secrets of the Underbelly of the Internet: A Comprehensive Guide to Monitoring the Dark Web
Monitoring the dark web is essential in today's digital age. However, is it possible to delete information from this hidden part of the internet? It's crucial to take measures to protect yourself, such as avoiding answering calls from unknown numbers and using a Caller ID and message filtering app like Truecaller. For more information on staying safe while browsing, check out other articles in the Secure Browsing section.
DigitalStakeout Scout is a NIDS solution that scans for unusual activity on networks and cross-checks against a database of known suspicious addresses. This monitoring dark web tool enables you to take appropriate steps to safeguard your privacy and mitigate the risk of cyber threats, such as identity theft, which can result in severe financial and social consequences. Key features of this solution include the ability to detect attacks on networks, trace the sources of attacks, and protect your brand's reputation. We highly recommend DigitalStakeout Scout for its robust security capabilities and comprehensive coverage of network activity.
Conducting Dark Web monitoring is crucial for individuals and businesses to protect themselves from potential security breaches and data leaks. One aspect of this monitoring can involve scanning the Dark Web for any mention of a specific email address. By doing so, individuals and organizations can be alerted if monitoring dark web their email address has been compromised and take necessary actions to secure their accounts and sensitive information. This Dark Web scan can be done for free using various online tools and services available.
If you're looking for a way to keep tabs on the dark web, there are some key features to look for in a monitoring tool. One of the most important is a free search facility, which allows you to search for specific information using keywords or phrases. Another useful feature is an alert utility, which will notify you if your search criteria is matched. You should also look for a tool that can search on email addresses and telephone numbers, as these are often used as identifiers on the dark web.
When you conduct a search, the results will show all data leak events that involved the email address or telephone number you entered. This information can be used to determine if your personal data has been compromised and if your email address has been listed in any Dark Web attack lists. Staying informed about these types of events is essential for protecting your online security and privacy.
The best dark web monitoring tools available today are largely automatic, which means they can continuously scan the dark web for new threats without any manual intervention. These tools use sophisticated algorithms to detect potential threats and alert you to any suspicious activity. This makes it easier to stay on top of the latest security threats and take action to protect yourself.
It's worth noting that the name TOR, which stands for "The Onion Router", was originally used to describe one of the first dark web networks. Today, there are many different networks and tools available for monitoring the dark web, and it's important to choose one that meets your specific needs and requirements.
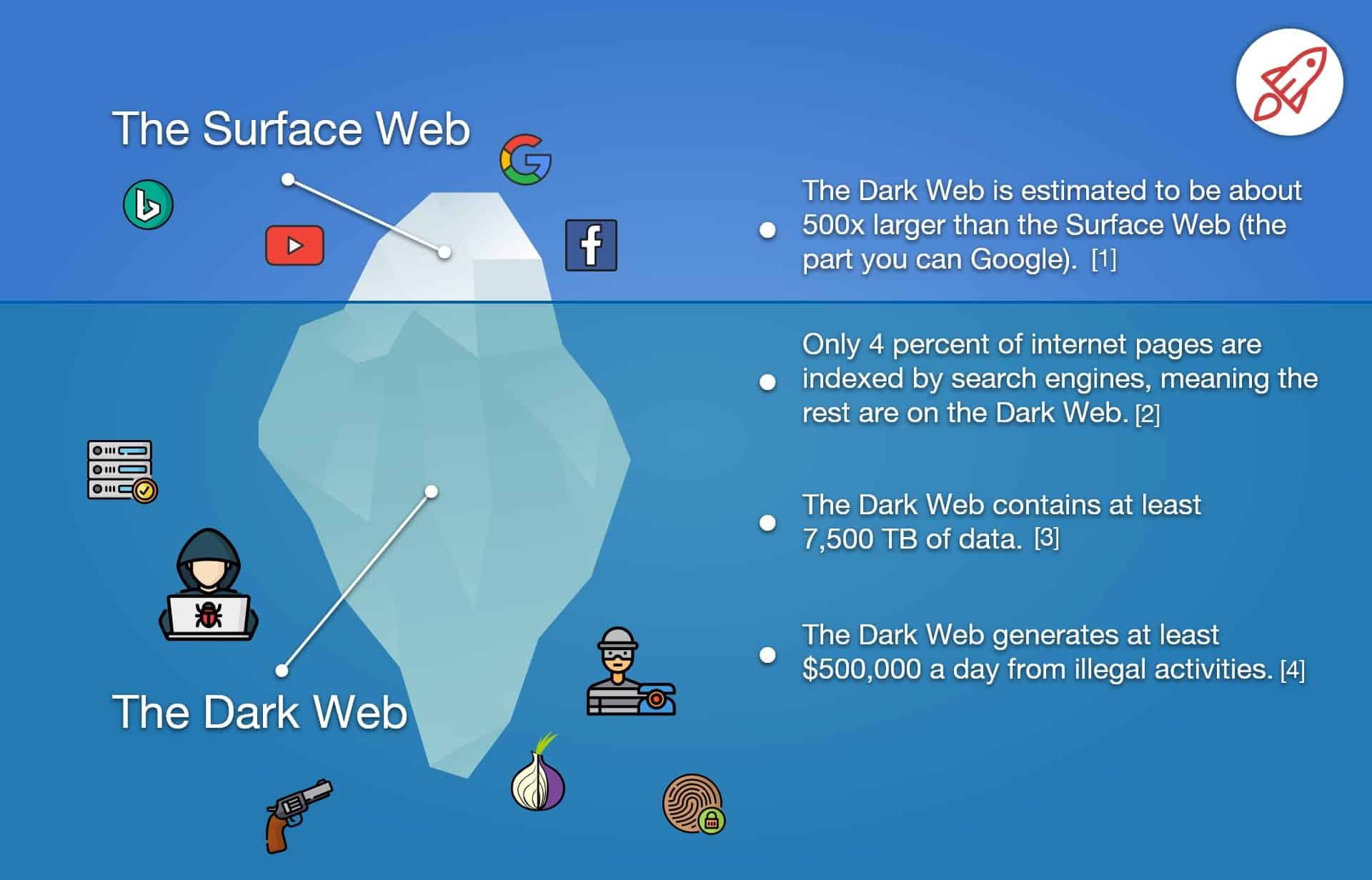
Monitoring the dark web is a crucial aspect of modern cybersecurity. It involves tracking and analyzing online activity on hidden websites and encrypted networks that are not indexed by standard search engines. By monitoring the dark web, cybersecurity professionals can detect potential threats, such as stolen data, malware, and illegal activities, before they cause harm to organizations or individuals.
One of the challenges of monitoring the dark web is the need for specialized tools and expertise. Unlike the clear web, the dark web is not accessible through a web browser, and it requires specific software, such as Tor or I2P, to access. Moreover, the anonymity and encryption of the dark web make it difficult to trace and monitor malicious activity.
To overcome these challenges, cybersecurity professionals use various techniques, such as data scraping, machine learning, and human intelligence, to collect and analyze dark web data. They also collaborate with law enforcement agencies and other organizations to share information and coordinate their efforts.
In conclusion, monitoring the dark web is an essential part of modern cybersecurity, and it requires specialized skills and tools. By staying vigilant and proactive, cybersecurity professionals can help prevent cybercrime and protect their organizations and clients from potential threats.
Initiate a 15-day complimentary assessment to begin monitoring the dark web. The financial institution that employed the compromised ATM blueprint was the concerned party. Additionally, Gmail accounts can also be monitored through this service.
Discovering the Secrets of Dark Web with Deep Web Entry
For small businesses with limited financial resources, it is advisable to consider alternative services rather than completely disregarding the importance of monitoring the dark web. Digital Shadows SearchLight offers comprehensive protection with a particular focus on safeguarding the reputation and brand image of its clients. Tor represents a reliable web security solution.
Norton LifeLock is a leading tool for monitoring the dark web. Certain sites and forums on the dark web are utilized by hackers to purchase, sell, and exchange stolen data from businesses, particularly login credentials, personal identity information such as social security numbers, and financial account details like credit card numbers.
When it comes to monitoring the dark web, the stakes are higher when it involves passwords for banking or social media accounts. We conducted a comprehensive examination of NordVPN's privacy policy and found that it adheres to a strict no-logs policy. Additionally, this service is cloud-based and allows access to the Dashlane customer dashboard via a web browser or mobile app.
Monitoring the dark web is a crucial step in ensuring the security of your business. By keeping an eye on this hidden part of the internet, you can spot data that has been leaked from associated businesses, giving you a heads up on any potential attacks. This provides you with valuable time to take action and protect your company's sensitive information. Additionally, the dark web is a vast data pool that can be analyzed using search facilities, providing insights into the latest trends in cybercrime. This information can be used to issue industry-wide and general threat warnings, enabling you to stay ahead of the game. Customizable threat alerts also provide an extra layer of protection, ensuring that you are notified of any suspicious activity as soon as it is detected. However, the downside is that the responsibility of monitoring the dark web falls on you, requiring vigilance and expertise in the field of cybersecurity.
Shining a Light on the Dark Web: A Guide to Deep Web Links
If your phone number gets leaked on the dark web, it can have serious consequences. It is not enough to conduct periodic scans of the dark web as this may not be effective in protecting your business from being exposed as soon as your network credentials are published. Monitoring the dark web on a regular basis how to get on the dark web on iphone is crucial to safeguarding your personal and business information from unauthorized access and use.
Even if you have taken all precautions to protect your personal information, there is still a chance that it could be exposed on the dark web. As a result, monitoring the dark web has become more crucial than ever for both individuals and businesses alike.
Explore further
Distributed by Key-licious, LLC.